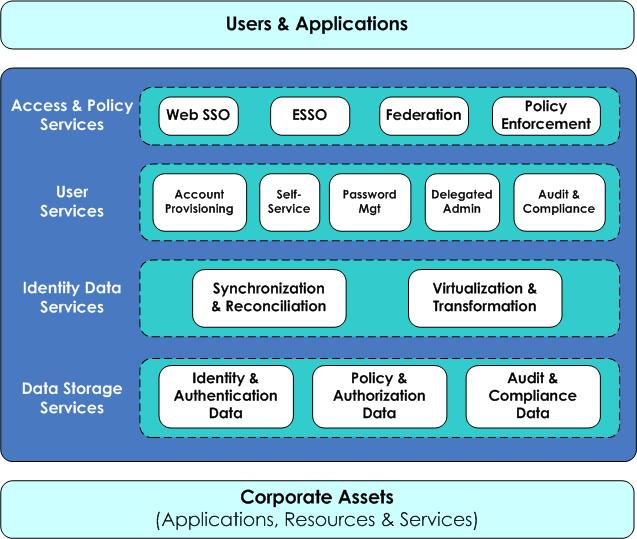
Identity Services
The Identity Services industry has used many terms to describe the overall umbrella under which all (or most) of its products and services fit. Among them are Directory Services, Identity Management, and Identity & Access Management with Identity Management being the most widely used term. Since Identity Management has come to be used in many cases specifically for user provisioning and delegated admin... And since an identity platform typically provides a service out to the larger organization... And since the larger IT industry is moving toward a software-as-services model... it makes sense to me that we start using the phrase Identity Services to describe the umbrella under which our products and services fit.
The Identity Services layers are:
- Access and Policy Services
- User Services
- Identity Data Services
- Data Storage Services
Access and Policy Services
This is the layer at which policies and access permissions are enforced. As people attempt to access resources throughout an organization, this layer grants or denies access based on user identity information and access policies.
The Access and Policy services layer relies upon the identity data services and data storage layers to provide accurate and up-to-date information about users, rights and policies. The user services layer relies upon this layer to control access to its own services.
Commonly found in this layer are Web SSO and Enterprise SSO applications. But implementations vary widely. In the past, access management was handled individually by each individual application. It was difficult to manage and control. The ideal future-state scenario is to have a single centralized enterprise access control platform that every application would leverage. Most organizations today that have already begun to offer identity services are somewhere in the middle.
Emerging technologies in this layer include federation products and standards, network-based access control, user-centric solutions and standardized policy management infrastructures (XACML).
User Services
User services include software and services that enable business efficiency and functionality. Generally, services at this layer are driven by user interaction. Managers manage their employees, grant and deny access, perform attestation duties and run audit reports. System users manage their own information, reset and recover passwords and request access permissions.
The user services layer relies upon the access and policy layer to ensure that people can only perform operations to which they're entitled. It relies on the identity data services layer to achieve the proper view of the data it needs to act upon. And it obviously relies on the data storage layer to store the results of operations performed at this layer.
Typical applications found in this layer include user provisioning and deprovisioning systems, password reset and recovery applications, access management tools and audit reporting. The majority of traditional Identity Management and Identity Services projects and discussions are based in this layer.
Technology emerging in this layer includes advanced attestation reporting, improvements to provisioning, workflow, self-service and password management services and web service enablement.
Identity Data Services
The identity data services layer provides vital services to the overall identity services infrastructure. At the top two layers (access & policy services and user services), systems interact with data that resides on the data storage layer. Each system and application has its own set of requirements and its own data needs. This presents a great challenge for organizations implementing identity services. Identity data is spread out across organizations in network OS and email systems, HR systems, application databases, identity-specific directories and more. This layer provides identity services and applications access to those heterogeneous and disparate data stores in an organized and controlled manner.
The identity data services layer relies upon the access & policy layer to present valid credentials for the user, service or application requesting data access. It presents data out to the access & policy and user services layers but its primary interaction is with the data storage layer where its job is to act as a librarian of sorts. It catalogs identities across systems, joins accounts in multiple systems and presents the data in the format and structure requested by its consumer.
Metadirectories and data synchronization tools have traditionally ruled this layer. Many companies have made progress in identifying identity data throughout their organization and using synchronization products to create reliable sources for identity. Some companies create an enterprise directory that stores a common attribute set that is available to the identity services infrastructure for consumption. Others use synch tools to maintain the existing data stores. Typically, though, there are challenges associated with allowing applications and services to directly access your organizations data stores. Enter Virtual Directory technology. Virtual directories have been steadily proving their worth and will likely emerge as the dominant technology in the identity data services layer. A virtual directory can present a virtualized view of identity data out to the identity services infrastructure for consumption. The view can be customized based on the user or application making the request and can be transformed into multiple formats as appropriate for each consumption point.
Emerging technologies at the identity data services layer includes additional built-in connectors for meta- and virtual directories as well as adoption of emerging protocols and standards.
Data Storage Services
The data storage services layer is the simplest to understand. Organizations have had this layer in place for years. This layer holds the databases, directories and other data storage systems that hold identity data throughout the organization. Typically, there are many different types, structures and sizes of identity data stores in a single enterprise.
The data storage services layer may interact with each of the other layers to provide identity data as appropriate. In some cases, the data storage layer is masked by the identity data services layer so that the upper two layers do not directly interact with the data storage layer.
This layer is by far the most mature in terms of technology and adoption. LDAP directories and relational databases have proven their usefulness and are well understood amongst IT professionals. The implementations are as plentiful as the organizations that rely upon them.
Emerging technologies in this area include the adoption of new data storage standards, data virtualization (not to be confused with virtual directories), improved security & encryption and general feature & functionality improvements.